Beware – Dangerous IoT Attacks Leads Some One to Hack and Control Your Car
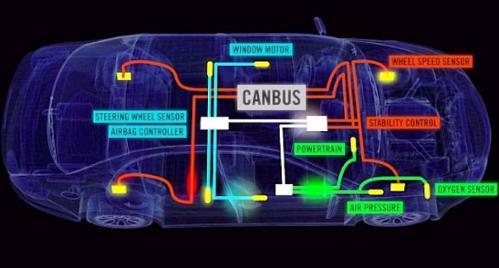
The Internet of Things (IoT), responsible for connecting unthinkable things, now offers the possibility of connecting vehicles to the internet. With this, great advantages are obtained, among others, to increase the security of those who are in their interior by providing real-time information on traffic conditions, incidents on roads, climatological risks and any type of data relevant to our safety and comfort.

Having the vehicle fully connected implies that if we detect that someone has stolen it we can turn it off immediately or if for some reason we are unable to continue driving the car, someone you trust can remotely do so while the driver recovers, being possible with new developments, that the car can go independently to the nearest shelter or hospital in case of emergency.
But like everything connected to the Internet, a poor security configuration or poor programming of the devices open the possibility of an attack that alters the functions of the vehicle, remotely gaining control of it, performing a remote hijacking or theft, block the doors or immobilize the vehicle in the middle of a road.
On the internet, a researcher can find about forty million industrial vehicles, which can be located and controlled in real time without the need for advanced knowledge due to its poor configuration. We are talking about devices that do not require a user and password to connect to them and control them remotely.
For security reasons, we can not give more details about these vehicles, but if any researcher feels interested in this issue, we can always discuss it.
Insurance companies charge their policies by setting prices according to statistics, driver age, vehicle color, the age of the driver’s license and driver’s gender among other data. But all those patterns to consider lose value if we think about the new risks that are generated when connecting our vehicles to the internet.
The implications of cyber attacks are wide, and it seems that no insurance has taken action in this regard, nor do they value this type of information when granting the policy.
The advantages of cyber attacks vehicle to the internet are very broad, but we must be able to minimize the associated risks and make them less attractive to attackers in order to maximize the safety of the driver, passengers, pedestrians, other drivers and the vehicle itself.
We must be aware of the associated risks and put means to ensure an optimal level of security
Quoting Ph.D. Jesus Friginal, there is clearly “the need to formalize and execute the functional and non-functional tests that a system needs to be valid. A functional test should not only demonstrate that a system does what it should, but DO NOT do what it should NOT.
A non-functional test must verify that the system will operate under stress, safety, etc. conditions, bringing the system to a known and controlled state in case of any eventuality.
Source & Credit: This article provided to www.gbhackers.com by Claudio C , SCASSI, Spain. He Would like to share his knowledge, for the readers who are interested in exploring tacts and trends.All the Content of this Article Belongs to Original Author Claudio C, SCASSI, Spain. www.gbhackers.com won’t take any credits.
Read full news article on GBHackers